Package Management
CMPR: Signs You’re a Level 4 in Package Maturity
This article is 4/5 in our series on Centrally Managed Package Repositories, also available as a chapter in our free, downloadable eBook Package Management at Scale
If an organization reaches this level, it’s never by accident. It’s a result of deliberate investment in automation, strong governance, and repeatable systems. This level reflects high maturity across package management, security, and developer enablement.
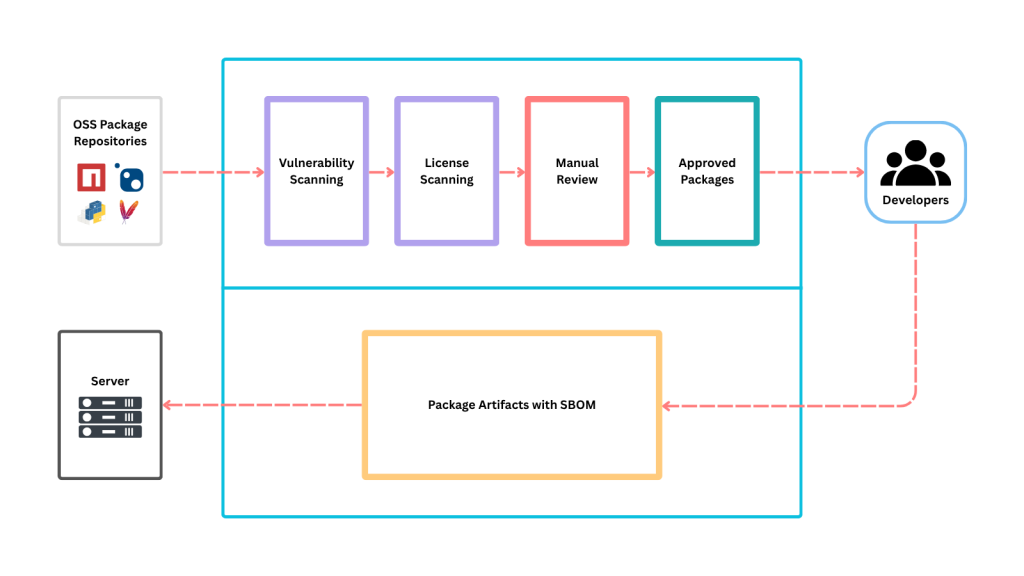
At this level, package management isn’t just a supporting tool; it’s a core platform capability. All modern components used across the organization are stored as packages in a centralized, purpose-built package management system, with some exceptions like legacy systems or niche package types. Niche and legacy packages may be better isolated or eventually replaced with modern equivalents, as they often lack compatibility with current tooling, security practices, or deployment workflows. However, some legacy tools remain critical to business operations and cannot be easily replaced, so they may need to live in silos or be integrated through specialized solutions. They’re organized into feeds and feed groups that reflect business domains or trust levels. Access to those feeds is tightly controlled. Developers, automation tools, and CI servers have the right permissions to the right packages, and nothing more.
Security and compliance checks are integrated into the workflow. Every package is scanned for vulnerabilities and license compliance before it ever reaches a developer or production environment. Only approved packages are visible or installable. Curation is no longer a manual gatekeeping process. Most of it is handled automatically by policy-driven workflows, allowing teams to move fast without sacrificing safety.
Every artifact is cached, versioned, and named using consistent semantic versioning (SemVer) standards. Builds are reproducible, environments are predictable, and incident response is faster because package flows are transparent and traceable.
In this chapter, we’ll look at what it means to operate with fully realized, deeply integrated practices across all five pillars, and the benefits this brings:
| Centralization | All packages are discoverable and managed from a single source of truth, enabling consistency, auditability, and efficient reuse. |
| Governance | Access is role-based and policy-enforced. Security, compliance, and licensing controls are embedded—without slowing anyone down. |
| Curation | Automation ensures only trusted, verified packages are available to teams. Policies handle routine vetting, so humans don’t have to. |
| Distribution | Package flows are structured, secure, and transparent. CI systems retrieve from authorized feeds, and caching improves performance. Packages traceable from source to deployment. |
| Scalability | Tooling and process scale with the organization. Onboarding is fast, integrations are smooth, and collaboration is streamlined. |
Developer Enablement: Refined Delivery Through Automation, Reuse, and Secure Defaults
At this level, teams operate in an environment designed to remove friction and boost velocity. Developers aren’t burdened with infrastructure setup or manual governance—they’re empowered to focus on building.
✅ Access to Only Approved Packages: Developers automatically work within secure, approved environments by having access only to feeds containing pre-approved packages. Package promotion ensures that all dependencies are vetted before developers pull them into their IDE, reducing the risk of unsafe components and removing the need for manual approval or last-minute reviews.
✅ Policy-Based Security: Security is enforced through configured policies for SCA and access. Developers don’t need to worry about scanning dependencies or tracking license risks. These are handled by pre-established policies, ensuring compliance without creating bottlenecks. At level 4, you might have only global policies – same policies for all projects and teams, with occasional manual override from approved to denied and vice versa.
✅ Central repositories, not per-project: Centralized repositories remove the need to configure or manage individual package sources for every new service or team. This saves time, reduces errors, and ensures consistency across projects, making onboarding smoother and scaling easier.
✅ Reuse of Internal Packages: Standardized and configured access to internal package feeds encourages reuse across teams and services. Rather than reinventing the wheel, teams can leverage approved packages and dependencies. This improves consistency, reduces risks of bugs and vulnerabilities, and accelerates delivery timelines.
✅ Semi-Automated Compliance to SemVer: Versioning rules are enforced through CI/CD pipelines, helping teams follow semantic versioning practices. This approach helps teams maintain predictable versioning. As a result, dependency upgrades are safer, reducing the risk of breaking changes and enabling more reliable collaboration across the organization.
These capabilities transform package management from a manual, error-prone process to one that allows teams to move faster, stay secure by default. They spend more time shipping features and less on managing infrastructure.
Security: Trust Through Automated Workflows and Centralized Control
Effective security starts with centralized control and automated policies that keep risky packages out of your development process.
✅ Package Approval Workflows: Centralized repositories use two distinct feeds: an unapproved feed that proxies OSS packages pending review, and an approved feed containing only vetted, production-safe packages. Packages go through a formal approval process before becoming available, ensuring thorough review without slowing down development. This setup ensures developers only access trusted packages that have been assessed and approved.
✅ Developers Access Only Approved Feeds: Configured permissions restrict developers to approved feeds, preventing accidental use of unvetted or risky packages, and enforcing organizational policies concerning vulnerabilities and licenses.
✅ Automated Policy-Based Vulnerability and License Scanning: Continuous automated scanning checks all packages for vulnerabilities and license compliance. These block unapproved or risky packages or dependencies before they reach development or production environments.
✅ Shorter Mean Time to Remediate (MTTR) Zero-Day Vulnerabilities: Using Software Bill of Materials (SBOM) data, organizations can quickly identify affected packages and restrict access. This enables faster response and remediation of critical vulnerabilities.
With these practices, security becomes a seamless, automated part of development, protecting your software without blocking progress.
Governance: Standardize Package Flow Without Slowing Teams
Governance is built into the package lifecycle through automated policies, access controls, and structured CI/CD pipelines that enforce consistency and traceability.
✅ Repackaging for Controlled Promotion: Repackaging transforms tested pre-release packages into stable, production-ready versions without changing their contents. As packages move through CI/CD stages (e.g., from -ci.8 to -rc.8 to 1.0.0), audit trails are embedded directly into the package. This ensures traceability while allowing teams to promote verified builds without rebuilding or introducing drift.
✅ Access Control: Task-based permissions are tied to users or groups, scoped by feed, feed group, or globally. With internal or external directories (like LDAP/AD), you can manage who can publish, promote, or view packages, enforcing least-privilege access and maintaining control across environments.
✅ LDAP Integration: Active Directory and OpenLDAP integration exists. This allows you to manage user access with existing accounts and groups. This supports role-based access control (RBAC), eliminates the need for separate credentials, and ensures users receive the correct permissions based on their organizational roles.
✅ Semantic Versioning (SemVer) Enforcement: SemVer is used with structured pre-release labels (e.g., –ci.1, -rc.1) instead of mutable tags like latest or alpha. Pre-releases are repackaged into stable versions (e.g., 1.2.0-rc.1 → 1.2.0) in CI/CD, ensuring only tested, production-ready packages are deployed. This approach avoids dependency confusion, reduces breakage, and enables safe, scalable collaboration.
With these controls, governance shifts from a manual burden to a reliable, embedded process. This enables speed, consistency, and compliance by default.
Auditability: Clear Insights Through Transparent Package Tracking
Comprehensive auditing provides the transparency and control organizations need to maintain security, ensure compliance, and optimize package management.
✅ Know The Who, What and Where of Package Use: Organizations will have detailed insights into package downloads, tracking exactly who accessed which packages, where they are deployed, and how frequently they’re used. This granular visibility helps teams identify critical dependencies, spot unusual activity early, and make informed decisions about package updates or retirements. Feed-level and global usage stats enable better capacity planning and security posture.
✅ Repackaging with History: All repackaging is fully recorded, capturing who initiated the change, the source package version, the timestamp, and the new stable version. This creates an immutable audit trail that ensures accountability and supports root cause analysis in case of incidents. Maintaining this history reduces risk by enabling quick rollback or investigation when issues arise.
✅ Software Bill of Materials (SBOM) and Traceability: Organizations import and export SBOMs using the OWASP CycloneDX standard, listing all components, versions, licenses, and vulnerabilities for compliance and security. Imported SBOMs create or update projects and releases, add packages, and trigger issue analysis. While best for tracking in-house software, third-party SBOMs may show missing packages. Exported SBOMs merge metadata with imported details, creating detailed reports to support audits and improve software supply chain traceability.
Together, these audit features empower teams to move quickly and confidently, balancing agility with control and compliance.
Scalability: Designed for Growth with Replication, High Availability, Load Balancing
At this level, organizations may not yet have a fully scaled infrastructure: no hybrid cloud setup, on-prem replication for redundancy, high availability, load balancing, or global multi-site replication to efficiently distribute packages to edge nodes abroad. But with effective scalability, you can implement these quickly, when and if you need to. Scalability doesn’t mean you’re already scaled, it means you’re positioned and ready to scale as demands grow.
✅ Centralized Repository and Governance: A unified source of truth eliminates version conflicts and duplicated efforts across teams and locations. This consolidation simplifies management, enhances security, and streamlines auditing by keeping all packages and access policies in one place.
✅ Replication and High Availability: Managing multiple siloed registries means figuring out how to implement high availability, load balancing, replication, and other scaling mechanisms for each tool individually—assuming they even support those capabilities. In contrast, with a centralized repository, you only need to configure these scaling mechanisms once. But the time savings isn’t just about doing “one vs many.” Purpose-built package managers designed for scale often include built-in support for HA, LB, and replication, making setup faster, more reliable, and easier to maintain.
By centralizing management and supporting replication, high availability, load balancing, and edge deployments, this approach ensures your infrastructure can confidently scale to meet future demands.
Moving Forward: Optimizing with Enterprise-Grade Package Management
As organizations mature in their package management journey, the focus shifts to optimizing reliability, availability, and performance at scale. Challenges like downtime risks, uneven load distribution, and latency issues can undermine even well-governed environments if not addressed proactively.
🚀 High Availability & Load Balancing: Implementing HA architectures and load balancing ensures continuous access to packages, minimizes disruptions, and maintains performance under heavy demand. These capabilities reduce single points of failure and distribute traffic effectively across infrastructure.
Why this helps: High availability and load balancing boost system resilience and responsiveness. This allows teams to rely on stable package delivery pipelines even during peak usage or infrastructure failures.
🚀 Edge Deployment Readiness: Distributing package feeds closer to development teams through edge deployments reduces latency and improves download speeds. This is especially key for globally dispersed organizations.
Why this helps: Edge deployment readiness ensures developers can access packages quickly and consistently, reducing wait times and bottlenecks. This improves productivity, accelerates testing and deployment, and keeps teams aligned across different regions.
🚀 Global and Local Policies: As your team scales and learn specific policy requirements of each project and team, you will have locally customized policies and reach level 5.
Why this helps: Edge readiness accelerates development cycles by delivering content faster and more reliably, enhancing developer experience and productivity regardless of location.
By advancing to enterprise-grade package management with built-in HA, load balancing, and edge support, organizations create a robust foundation that supports ongoing growth, operational excellence, and innovation. This level of maturity turns package management from a potential bottleneck into a seamless enabler of continuous delivery at scale.
How Do You Compare? Assess Today, Strategize for Tomorrow
Understanding your organization’s package management maturity can be difficult when relying only on internal perspectives. Blind spots, untested assumptions, and the lack of benchmarking make it easy to miss important details. A guided assessment with our team brings an outside perspective, helping you uncover risks and opportunities you might not see internally.
You can schedule your assessment directly from our homepage:
The resulting report will place your practices within our maturity model, giving you a clear strategic overview as well as detailed, actionable guidance for each level.
Meanwhile, you can download our free guide that this article came from, Package Management at Scale. It offers a preview of upcoming content, practical insights into centralization, distribution, and curation, and a rubric to assess your team’s maturity. Download your free copy today!
