Package Management
How Downloading Without Curation Leads to Security Risks
Many teams pull open-source packages into their projects without thinking twice. They might stash them locally, pass them around through CI pipelines, or build and test on their own. But without internal repositories or any guardrails in place, each team ends up working in its own bubble.
That kind of flexibility can feel great at first, but without centralized oversight or controlled dependency management, things can get risky fast. Organizations lose track of which packages are being used and where, which opens the door to vulnerabilities and potential data breaches. Curated feeds (along with automated scanning and vetting) help close those gaps. When teams review and approve packages before using them, they make sure only trusted dependencies make it through, cutting down on security and compliance issues.
In this article, I’ll break down why unmanaged package use is such a problem, how curated feeds with scanning and vetting can keep risks in check, and how ProGet can help you review, scan, and approve packages to keep your software supply chain secure and compliant.
How Poor Dependency Management Invites Risk
When teams pull packages straight from OSS registries without internal repos, standards (or any real oversight), it becomes almost impossible for organizations to keep track of what’s actually going into their code. That lack of visibility into incoming dependencies can lead to security and compliance issues:
⚠ Vulnerable packages slip through unnoticed, and without policies to block risky packages, the same issues often reappear across multiple projects. The 2025 Black Duck report found that 86% of codebases had vulnerable OSS components, most of them high or critical. That kind of exposure can open the door to breaches and data loss. A single vulnerability might get fixed in one application but linger in another for years, leaving the organization exposed and slowing down threat response.
⚠ Licensing is another major concern. Teams can unknowingly introduce packages with incompatible licenses. This creates legal risk, audit failures, and costly remediation when compliance gaps are discovered later in the development cycle. These gaps can seriously damage your reputation and interfere with how your organization runs.
⚠ Fragmented dependency management makes it harder to respond to security incidents. When security teams can’t see which apps rely on which components, investigations slow down and potential entry points stay hidden. Those blind spots often become costly, leading to avoidable breaches and downtime. Plus, the longer an issue lingers, the worse it gets. IBM’s 2024 Cost of a Data Breach Report found that it takes nearly 287 days on average to contain a breach. This drives up remediation costs and amplifies organization-level damage.
Without centralized oversight or dependency control, these problems multiply. Each team is left to manage its own dependencies, resulting in a patchwork of inconsistent practices. The solution? Curated feeds with vetting and automated scanning that make sure every package is reviewed, approved, and trusted before it reaches production.
Curating Feeds with Scanning and Approval Workflows
Unreviewed packages are a major source of vulnerabilities and quality issues, and it only takes one bad dependency to put an entire app at risk. The best way to prevent this is to review and approve packages before they’re used. With a curated feed, all open-source packages flow into a single internal repository where they’re vetted for quality, licensing, and security. Only those that pass are promoted to an approved feed. This makes sure your developers work only with trusted components.

Automated vulnerability scanning adds another layer of protection. By setting severity-based rules, organizations can automatically block unsafe downloads before they reach a dev’s machine or a CI/CD pipeline. Teams can focus on building features, knowing that the packages they use are already cleared for safety and compliance.

When combined, scanning and approval workflows provide powerful protection. Vulnerabilities are blocked long before they reach production. With ProGet, these processes become even easier to implement at scale, giving you enterprise-grade visibility, control, and automation over every package that enters your environment.
Setting Up Package Approval Vulnerability Scanning with ProGet
ProGet’s approval workflow works by creating two distinct feeds: an unapproved feed, where new OSS packages are pulled in for review, and an approved feed, where only trusted, production-ready packages are stored.

Teams can review each package for quality, licensing, and security before promoting it to the approved feed.

This ensures that only safe, compliant components are used in builds. ProGet also automates compliance assessments to save time and maintain transparency. You can configure rules for how vulnerabilities are treated, whether to block, ignore, or flag them for review, and add notes for visibility across teams.
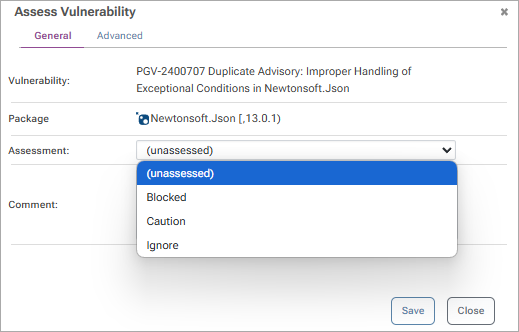
Automated vulnerability assessment lets you set rules based on severity levels (low, medium, critical, etc.), so you’re not forced to jump on every new issue the second it appears. You still have full control to review and tweak the assessment later.

With download blocking, only approved packages get through. Developers immediately know what’s off-limits, and if they try to grab a blocked package, they’ll get an error instead.

Scaling Securely with Curated Feeds
Without centralized oversight and controlled dependency workflows, organizations lose visibility into what’s entering their codebase, and with that loss of visibility comes risk. Vulnerabilities can slip in unnoticed, creating security gaps that grow over time.
Curated feeds with automated scanning and approval workflows eliminate these risks by ensuring that only reviewed, trusted packages make it into production. ProGet makes it practical to implement these controls across teams, giving you automation, visibility, and confidence in your software supply chain.
If this article resonates, check out our guide “Package Management at Scale”. It helps you review your current workflows and provides a practical roadmap for creating a secure, scalable package management strategy across all your teams. Download your free copy today!
Or, take the next step and implement a CMPR solution in your own organization using ProGet. You can start a 30-day free trial of ProGet Basic and see how centralized package management streamlines workflows, improves compliance, and boosts developer productivity firsthand.
