DevOps
Log4Shell Impact & Other High-Severity Vulnerabilities

If you’re a Java team, you’re almost certainly using Log4j, heard of Log4Shell, the new high-severity vulnerability, and are worried about how to deal with it.
On December 9th, CVE-2021-44228, a.k.a. Log4Shell was discovered and reported. Log4Shell is a high-severity vulnerability that affects the Log4j core function through a publicly available exploit. This vulnerability enables attackers to perform remote code execution and access all data on the affected machine. It also allows them to delete or encrypt files, holding them for ransom.
A large percentage of Java programs developed today use Log4j to log daily activities, users, and even passwords. Log4Shell allows attackers to also have access to this data. This Java vulnerability has the potential to wreck organizations and you might not even be aware that your team has it.
The good news is your Inedo products and instances are safe! We do not use Java to develop our products, and therefore don’t use Log4j — or this highly-vulnerable version.
However, your applications and many of your vendor applications could be at risk.
Dealing With Log4Shell
Dealing with CVE-2021-44228 is relatively easy – at least in theory: just upgrade to the patched version of the library on impacted applications. All of them. In production, development, and all other environments. On all servers. In all applications over possibly thousands of servers… then test your patches to make sure nothing breaks.
Regardless, the first step to deal with this vulnerability is to identify all the applications Log4j is being consumed by. You could do this manually or you can simply use a tool like ProGet’s package consumers feature.
Package Consumers uses pgscan or an API connection to let you know precisely where any given package is being consumed. This gives you invaluable insight into which specific versions of applications or components are consuming specific versions of your packages. If you discover a critical bug or security vulnerability, you can quickly identify the consumers and fix them or notify responsible parties, or simply delete it if it’s not in use.
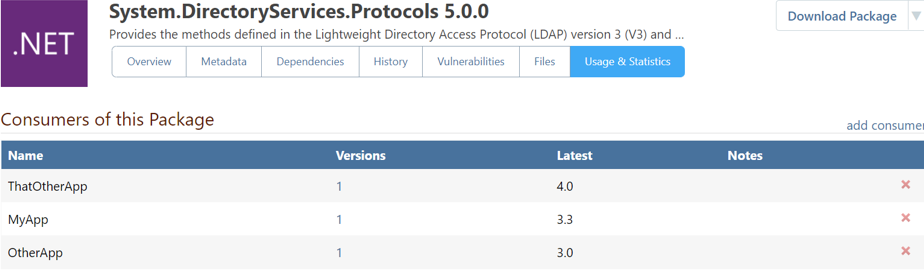
After identifying how and where Log4j is being used at your organization, patches can begin to roll out.
Using a tool to quickly locate and patch compromised packages could be the difference between a contained crisis and a complete organizational meltdown.
It’s important to note, CVE-2021-44228 is one of many vulnerabilities that are in your codebase. Introducing regular into your workflow could catch the next high-severity vulnerability early, giving your team time to patch and work around it.
Dealing With Future Vulnerabilities
Do vulnerability scans and do them often.
Manual vulnerability scans can be time-consuming but necessary to keep your code and organization safe. If you’re using a tool like ProGet’s integrated vulnerability scanning, it’s easy to assess package vulnerabilities by setting up customized auto-assessment rules.
ProGet can automatically block, allow, or flag vulnerable packages based on the severity level that you set.
ProGet comes with three built-in assessment types:
- Ignore: Indicates that the vulnerability report is not applicable or irrelevant and therefore allows for packages to be downloaded
- Caution: Tells developers to be careful to avoid the vulnerability; packages may be downloaded, but a warning is issued on the web UI
- Blocked: Means a vulnerability is too severe to allow use, and packages are prevented from being downloaded
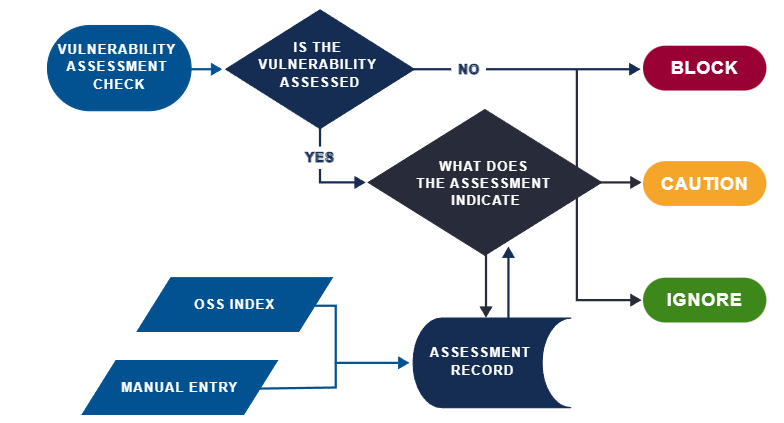
These rules are set by users and are based on CVE severity. Running the vulnerability scan would block CVE-2021-44-228 now that a high-severity vulnerability has been reported.
Protect Your Organization
These types of vulnerabilities allow criminals to cripple and ransom organizations. Without proper tools and systems in place, it’s possible your team is the next to lead the headlines.
We’ve created a helpful step-by-step guide for those interested in protecting their organization with a tool like ProGet. Read how you can protect your organization against vulnerability attacks like this now, and in the future.
